I’m what my boyfriend calls “a low tech girl.” I started having a Facebook account when I moved to the USA two years ago. If somebody has a chance to read this blog don’t think that Thai people are outdated. I always use Facebook to contact my family and my friends in Thailand. Most Thai people have Facebook accounts. Anyway, I try to update the new technology. Especially, I usually listen to the technology news from CNN.com while I am working at TJ library.
Recently, “Facebook Warns of New E-mail Scam [ALERT].” It is a massage from Facebook that reminds whoever has an account to pay attention to “new email-scam.” Not only hackers use facebook internal email system to sent out spam, but also they use the regular old school email spreaded the scam worldwide. Just let you know the risk that you may not expect. Because it can access any username and password used on that computer such as bank accounts, social sites, etc., you should find ways to protect yourself.
The news advises how to avoid scam as well. Follow these steps;
– Don’t open attachment and delete email.
– Install security software with anti-virus.
– Make sure security software is up-to-date.
I think technology is good although there are people use it in bad ways. You should always know what someone is up to.

For someone who may not know how to handle email scam…

Cloud vs. in-house
After I had attended the last class that includes cloud computing lecture by Ms. Shoptaw, I was motivated to do this blog. Begin with the definition of cloud computing, I believe that there are not many people who are familiar with this word. It is defined in a different way, for example, some analysts and vendors define cloud computing as an updated version of utility computing: basically virtual servers available over the Internet. Others argue that it is anything you consume outside the firewall is “in the cloud,” including conventional outsourcing. Based on Wikipedia, cloud computing is a way of computing, via the Internet, that broadly shares computer resources instead of using software or storage on a local PC.
Cloud computing allows consumers and businesses to use applications without installation and access their personal files at any computer with Internet access. This technology allows for much more efficient computing by centralizing storage, memory, processing and bandwidth.
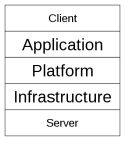
Cloud computing is broken down into three segments: “applications,” “platforms,” and “infrastructure.” Each segment serves a different purpose and offers different products for businesses and individuals around the world.
According to the recent article “Cloud vs. in-house: Where to run that app?,” Bill Claybrook covered the basic host-versus-outsource decisions that is usually made by IT managers, and the new options of public and private clouds, what was most interesting is the dilemma many in IT are finding around having new choices.
The best approach is the IT manager considering its company requirements first, and see if he can knock a few platform contenders off the list. He has to examine — in order — security, privacy, compliance, performance, and then features and functions of the platform so that he can knock public clouds out of contention quickly, if they aren’t a good fit. If public clouds are not an option, he can certainly build his own private cloud, leveraging virtualization technology to provide better server utilization.
In my opinion, there are some bad results of having cloud. It is bad enough when we lose our Internet connection for email and web surfing. But the recriminations will occur when the entire office grinds to a halt.
“Two-edged sword”
http://www.computerworld.com/s/article/9162542/Cloud_vs._in_house_Where_to_run_that_app_?

Cyberattack had control of more than 74,000 computers.
Over the past year-and-a-half, the criminals behind the cyberattack had control of personal, corporate and government computers at over 2,500 organizations around the world. These have been found to be zombies in the newly discovered “Kneber botnet.”
According to NetWitness, a computer security company headed by former DHS cybersecurity director Amit Yoran, discovered more than 75 gigabytes of stolen data during routine analytic tasks as part of an evaluation of a client network. The company said the data turned out to be the product of a botnet of over 74,000 computers, that the malware used to create the botnet was recognized by less than 10% of antivirus software, and that the botnet’s network communication was not recognized by existing intrusion detection systems.
The cache of stolen data included about 68,000 corporate login credentials, access to e-mail accounts, online banking sites, Facebook, Yahoo, Hotmail, and other social networking sites. It also includes almost 2,000 SSL certificate files, which are used for activities like online banking or connecting to a VPN.
Yoran suggests that this botnet makes Operation Aurora, the cyber attack directed at Google and 33 other companies last December, look unimportant. “While Operation Aurora shed light on advanced threats from sponsored adversaries, the number of compromised companies and organizations pales in comparison to this single botnet,” he said. “These large-scale compromises of enterprise networks have reached epidemic levels. Cyber criminal elements, like the Kneber crew, quietly and diligently target and compromise thousands of government and commercial organizations across the globe.”
As the botnet epidemic continues to evolve and potential negative ramifications become clearer, it is more significant than ever for employing consistent and proactive malware security measures. FireEye Malware Intelligence Lab outlines guidelines to combat global botnet epidemic.
Cyber crimes are relentless in their activities, and are continually fine-tuning their malware. Both individuals and organizations need to incorporate for minimizing the damage of data breaches due to malware. Stealth malware is an invasive element seeking to profit from illegal access into a network.

Words from Vivek Kundra
Based on the audio excerpts, Vivek Kundra, Federal CIO, plans to help push Federal IT towards more transparency and accountability. He talks about how he and the administration are transforming the role of technology in government — away from spending on infrastructure, and toward spending on its customer, the American people.
There are the four goals behind his work. First, Transparency and Open Government – President Obama has already signed a memo on the principles that government should be open, collaborative and participatory. Second, Engaging Citizens – beyond transparency and providing information that the private sector can use to innovate, the government should provide ways for citizens to actually be involved in daily government operations. Third, Lowering the Cost of Government Operations – Kundra wants to use technology more effectively by doing “a better job managing its more than 4 million employees and more than 10,000 IT systems”. Especially, he wants to change how investments are rationalized by focusing more on the outcomes and less on processes. The options to reduce the spending include greater adoption of cloud computing services and use of free and open-source technologies. Finally, Find the Innovative Path – the innovations that should be looked at need to focus on citizens, and be targeted towards providing services more efficiently. Technology should be thought of as an enabler, and a conduit towards the provision of services, rather than as a necessity in itself. Enabling Web 2.0 technology in government requires a change in mindset for many within government. These technologies focus on letting go of control, and being more collaborative and transparent in how government operations are conducted. Government must be more willing to take risks in order to innovate and become more efficient.

IT in my workplace.
I’ve been working as a student assistance clerical at Thomas Jefferson Library. IT is an important tool that I use everyday. To support the academic mission and long-term goals of the University, TJ Library provides various information resources. Current periodicals and bound journals located on level 5 are my responsibilities that I have to take care of. Every morning the mails arrive at the library, my duties are collecting, selecting, and sending to the respective departments. Later, I use Millennium serials to check in all coming journals into Merlin catalog. I also use Millennium serials to bind the complete volume of each journal and do a record of every bound journal.
MERLIN is the shared online library catalog for all of the libraries in the University of Missouri system. It informs you what items the libraries own. You can use several search options;
- type some search terms or a phrase into the main search box and click ‘search.’ (This is called a Keyword search.)
- Click any of the other types of searches for example, author, title, journal title, author & title, subject, number.
- try the Advanced Search option to combine or exclude terms and limit your results by year, location, material type, etc.

Have you ever heard about “Green IT”?
While most people worry more about environment currently, green computing or green IT that refers to environmentally sustainable computing or IT becomes the responsibility of the top CEOs. Using or disposing of computers, servers, and associated networking systems efficiently and effectively with minimal or no impact on the environment can help your business reduce operational costs, increase efficiency and boost productivity.
Green IT being recognized globally is down to the business benefits. ROI means everything to any company; for example Acer launched two new laptops, which were praised by Greenpeace as recyclable and virtually free of toxic substances. They are also designed to reduce energy consumption. Simultaneously, SAP released a sustainability performance management package in 2009 and plans to introduce some more sustainability-related supplemental software packages.